An Attacker Has Discovered That They Can Deduce
An ex-captain of the Salem militia is infuriated by the increase of crime on the streets HIS streets. Barbara awakes from her coma.

What Is A Side Channel Attack Wired
That night he makes his final heavy decision.

. We have to live with the fear and the uncertainty that everything can be taken from us in an instant. He is the son of the late Peter Gordon the nephew of the late Frank Gordon the. File uploads are pretty much globally accepted to have one of the largest attack surfaces in web security allowing for such a massive variety of attacks while also being pretty tricky to secure.
Because the pad like all shared secrets must be passed and kept secure and the pad has to be at least as long as the message there is often no point in using one-time padding as one can simply send the plain text instead of the pad as both can be the same size and have to be sent securelyHowever once a very long pad has been securely sent eg a computer disk full of. The main title voiceover by Steven Zirnkilton was also changed for one episode only to include the following dedication. Years later she is a participant of the Final Killing Game.
Forest information with Get-ADForest In a forest each domain has its own database and its own Domain Controllers. Criminals and lowlifes ran things. An attacker can use CSRF to obtain the victims private data via a special form of the attack known as login CSRF.
Pure Heroic Spirits the main body in the Throne. This implies that even if a domain can be autonomous without the need to interact with other domains it is not isolated from a security perspective. Known-plaintext attacks are possible when an adversary has access to both the plaintext and ciphertext of a message.
As the death toll in the Town rises his anger only grows as he finds the killers identity obvious. However users of a domain in the forest can also access to the other domains of the forest. As I know the family living there and how conservative they are with their cultural background I would not have expected that.
For the individual who originally used the alias The Calculator see Noah Kuttler. For the video game see Overwatch video game. She doesnt remember her talent at the beginning of the Killing Game so her title is the Ultimate.
Super High School Level. While no tribute can ever heal the pain of that day the producers of Law. From the first day I put on the badge I was told things could never change.
Imagine how I now just could now wait for the parents to make their big yearly holiday. The attacker forces a non-authenticated user to log in to an account the attacker controls. If the victim does not realize this they may add personal datasuch as credit card informationto the account.
You just showed me differentJim Gordon to Gotham Central James Worthington Jim Gordon is the commissioner of the Gotham City Police Department. Barbara was part of a group therapy that was overseen by Hugo. Before they can come up with any other plans Armin looks on in shock to find the Armored Titan still alive and ready to battle once more.
Servants are spirits made into special familiars of the highest rank referred to as Ghost Liners by the Mages Association that are bound to the MasterTypically Heroic Spirits under most systems they can also sometimes be Divine Spirits Phantoms Wraiths and living people depending on various circumstances. Awakening from her coma. This caused Barbara to awake from her coma as a nearby nurse discovers this and arranges for Hugo Strange to be informed.
He explains to the group that the Colossus Titan has become thinner compared to when it first transformed meaning that it will soon run out of. In the aftermath of 911 several cast and crew members volunteered to help the rescue effort. Kyoko Kirigiri 霧切 響子 is a student in Hopes Peak Academys Class 78th and a participant of the Killing School Life featured in Danganronpa.
If an algorithm is susceptible to these attacks the attacker can use this information to deduce the key which allows them to crack all of the other data that has been encrypted by the same key. Because thats the price we pay for choosing the people that we love Felicity Smoak to William Claytonsrc Felicity Megan Smoak July 24. On September 11 2001 New York City was ruthlessly and criminally attacked.
After some consideration Armin finally comes up with a plan. File Upload Vulnerability Tricks and Checklist. Although the Vigilante was fired for his violent and rash methods of war he still has a strong sense of justice or so he tells himself.
News of Jim Gordon being found guilty for the murder of Carl Pinkney was heard on the radio at Arkham Asylums medical wing. Batman has displayed surprising strength and can bench press weight of at least 1000 pounds and has personally stated that his maximum leg press weight is 2500 lbs over 1133 Kg. I can now deduce with reasonable certainty which of my neighbors home has a remote controlled sex toy in it.
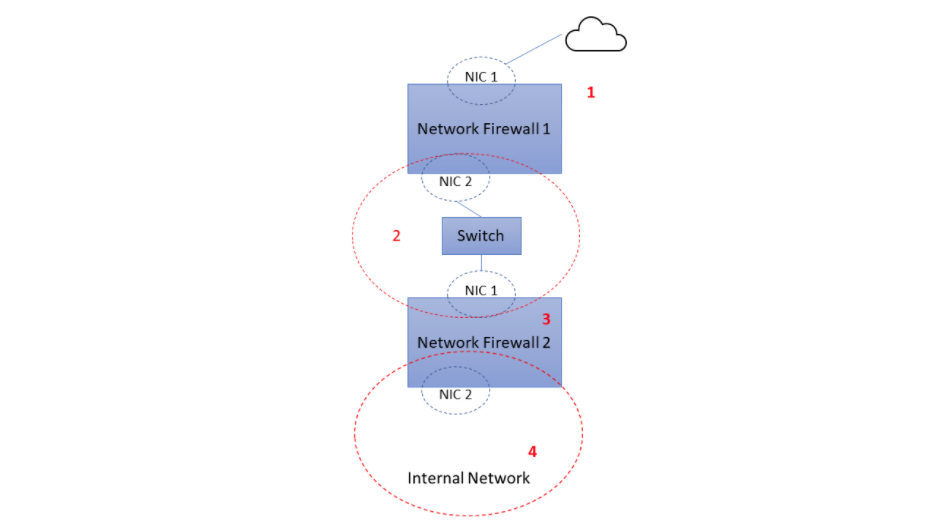
Linkedin Skill Assessments Quizzes Cybersecurity Quiz Md At Master Ebazhanov Linkedin Skill Assessments Quizzes Github

Linkedin Cybersecurity Assessment Solutions Coding Indian

What Is A Side Channel Attack With Examples

Attack Scenarios And Structures In Stuxnet Download Scientific Diagram

Cybersecurity Linkedin Skill Assessment Answer Linkedin Skill Assessment To The Innovation

The Guide To Identifying And Securing Pii Leakage Nightfall Ai
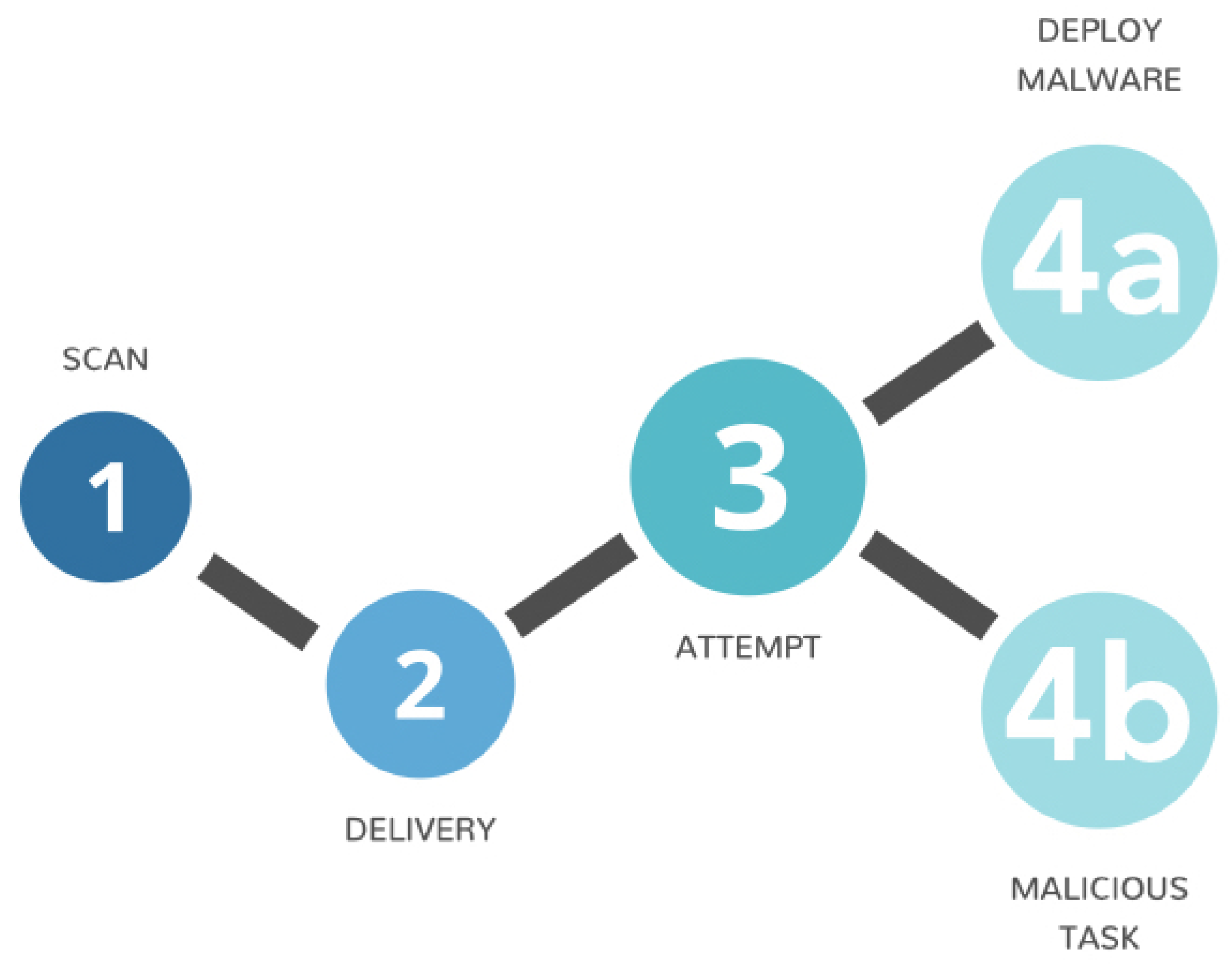
Information Free Full Text Early Stage Detection Of Cyber Attacks Html

Computer Security And Pgp What Is Bluedump Computer Security Bluetooth Device Cyber Security

Cybersecurity Linkedin Skill Assessment Answer Linkedin Skill Assessment To The Innovation

Cybersecurity Linkedin Skill Assessment Answer Linkedin Skill Assessment To The Innovation

Cybersecurity Linkedin Skill Assessment Answer Linkedin Skill Assessment To The Innovation
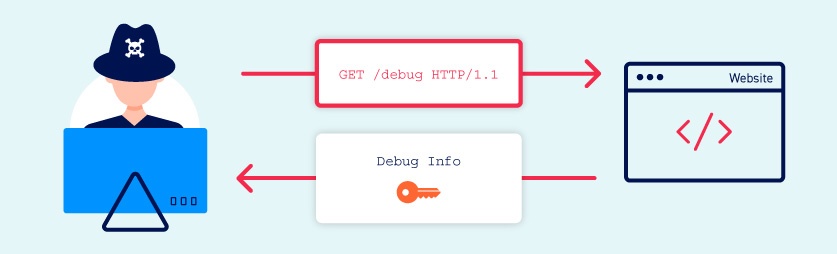
Information Disclosure Vulnerabilities Web Security Academy

Linkedin Cybersecurity Assessment Solutions Coding Indian

Plundering Of Crypto Keys From Ultrasecure Sgx Sends Intel Scrambling Again Ars Technica
Mysql Sql Injection Practical Cheat Sheet Perspective Risk

The Business Of Cybersecurity And Cyber Crime Pt 2 Reynolds Center

Linkedin Cybersecurity Assessment Solutions Coding Indian

Linkedin Skill Assessments Quiz Answers Cybersecurity 2022 Dipto Design

Comments
Post a Comment